Phishing attempts doubled in 2022 as scams, ransomware attacks continue to plague S’pore
Phishing attempts continued to plague the nation as reported cases more than doubled to 8,500 in 2022, said the Cyber Security Agency (CSA) in a report on Friday.
The surge is more than twice the 3,100 cases reported in 2021. In most attempts, fraudsters spoofed banking and financial services, as well as government and logistics-related services such as online shopping deliveries.
CSA’s 100-page report details the cyber-security threats faced in 2022, including the use of highly destructive malware in the Russia-Ukraine conflict, targeting industrial systems to cripple a nation’s vital services.
Threats have intensified in the past year, said CSA chief executive David Koh in the report.
“Away from geopolitical cyber security developments, scams continued to plague the local landscape,” he said. “The impact of cybercrimes such as scams is typically measured in financial loss, but the emotional toll it takes on individuals – such as anguish, confusion, and distress – is immeasurable.”
Phishing – designed to trick victims into handing over money or data – remains the top scam type here, with 2,918 phishing links taken down by the Singapore Cyber Emergency Response Team (SingCert).
More than 80 per cent of reported attacks spoofed a bank or financial service, spurred by the growth of online banking since the Covid-19 pandemic, said CSA.
June and September 2022 saw the highest number of phishing attempts in the banking and financial services sector.
More than half of these attempts saw China-based banks spoofed, although CSA noted that several of these banks do not have a presence here and would not have been known to most customers in Singapore. The fraudsters would typically send phishing messages to the masses in the hope of luring those with ties to such banks.
Second-most spoofed were government-related entities such as the Land Transport Authority and Singpass. Fraudsters would send phishing e-mails or SMS messages seeking payment for fines and other false claims to exploit users’ tendency to comply with messages from the authorities, said CSA.
The relevant organisations have since issued advisories to warn the public of such attempts.Spoofed websites and messages involving SingPost made up eight in 10 logistics-related scams. These scams are typically designed to dupe online shoppers by sending fake notifications about incoming parcels, or to urge them to pay for a made-up package held in transit.
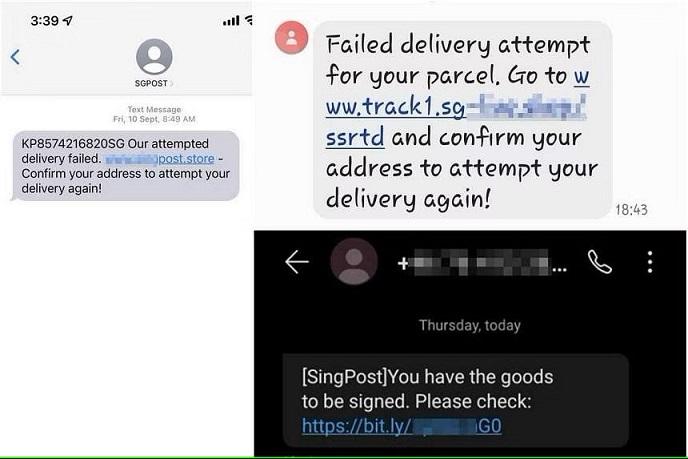
In most phishing attempts, attackers used links that end with “.xyz” – a domain registration that is relatively cheap and can be purchased by malicious actors in bulk to stage cyber attacks, said CSA.
The average length of reported phishing links also shortened by nearly half, suggesting that fraudsters are using URL shorteners, like bit.ly, to mask suspicious links and track the performance of each phishing site.
Ransomware – a cyber-security attack that locks up important data or digital services until a ransom is paid – fell by 4 per cent to 132 cases, but the number is likely to be much higher as not every company will admit to being attacked, said CSA.
Hackers mostly targeted small and medium-sized enterprises, particularly in the manufacturing and retail sectors, as many hold valuable data like intellectual property, which they can extort for money. Many of such firms also have limited cyber-security defences.
Attacks have proliferated with the rise of ransomware-as-a-service models, which allow anyone who can pay to stage sophisticated attacks, said CSA.

Ransomware groups have evolved over the years to become more business-like in their operations, with logos and branding on their ransom notes to cultivate a public profile, and call centre functions to help victims to make payment and unlock their files, said CSA.
And like real businesses, these groups are expected to scout for new markets to attack to boost ransomware revenue, said CSA, adding that it poses a threat to all industries. It urged firms to secure their systems and back up critical data regularly.
The authorities are working closely with critical services here to monitor cyber threats, which have intensified amid the Russia-Ukraine conflict, said Mr Koh.
Destructive malware targeting vital services of each side has caused worry internationally. “These attacks have already caused significant disruption to Ukrainian systems. The potential of their spread beyond the conflict zone is a catastrophic possibility,” Mr Koh added.
To tackle the rise in cases, Singapore formed a Counter-Ransomware Task Force in 2022, which pulls together senior officers from the CSA, the Ministry of Defence, the police and other organisations. The task force published a playbook in November 2022 on how ransomware attacks typically unfold and how to tackle them.
As a first line of defence, organisations should set up multi-factor authentication to make it tougher for hackers to gain access to systems even if the credentials are leaked, said CSA head of incident response and management Wayne Lim in CSA’s latest report.
Employees should also be trained to recognise phishing e-mails, while the organisation should configure alerts to notify staff of potential incidents, and create a plan on what to do in the case of a cyber attack, he said.
Get The New Paper on your phone with the free TNP app. Download from the Apple App Store or Google Play Store now
