Tools used by fraudsters in phishing scams easily found online
The tactics used by fraudsters in the recent spate of SMS phishing scams have been called sophisticated, but many of the tools used are easily available.
Checks by The Straits Times found that free or cheap tools available online can be used to send SMS messages that carry the same sender identification address as those used by legitimate banks and government agencies, which causes the fake messages to appear in the same thread as the real ones.
Here is a look at the known tools used in the recent scams.
Third-party SMS clients
While an SMS message sent from a mobile phone typically identifies itself as being from the user's mobile number, there are programs that send SMS messages over the Internet and mask the sender's number.
Paid SMS aggregator services such as Twilio are used by legitimate businesses to communicate with customers. Most allow the sender ID field to be customised with the name of the business instead of the default unfamiliar number.
Some countries require businesses to pre-register for sender IDs, meaning users have to provide information and supporting documents to an authority for approval. Singapore does not currently enforce pre-registration.
Using a service based in Europe, ST was able to send and receive SMS messages that appeared to be from banks such as UOB and Standard Chartered, as well as government agencies like the Ministry of Health and the Central Provident Fund Board.These messages appeared in the same thread as previous legitimate messages, including transaction notifications.
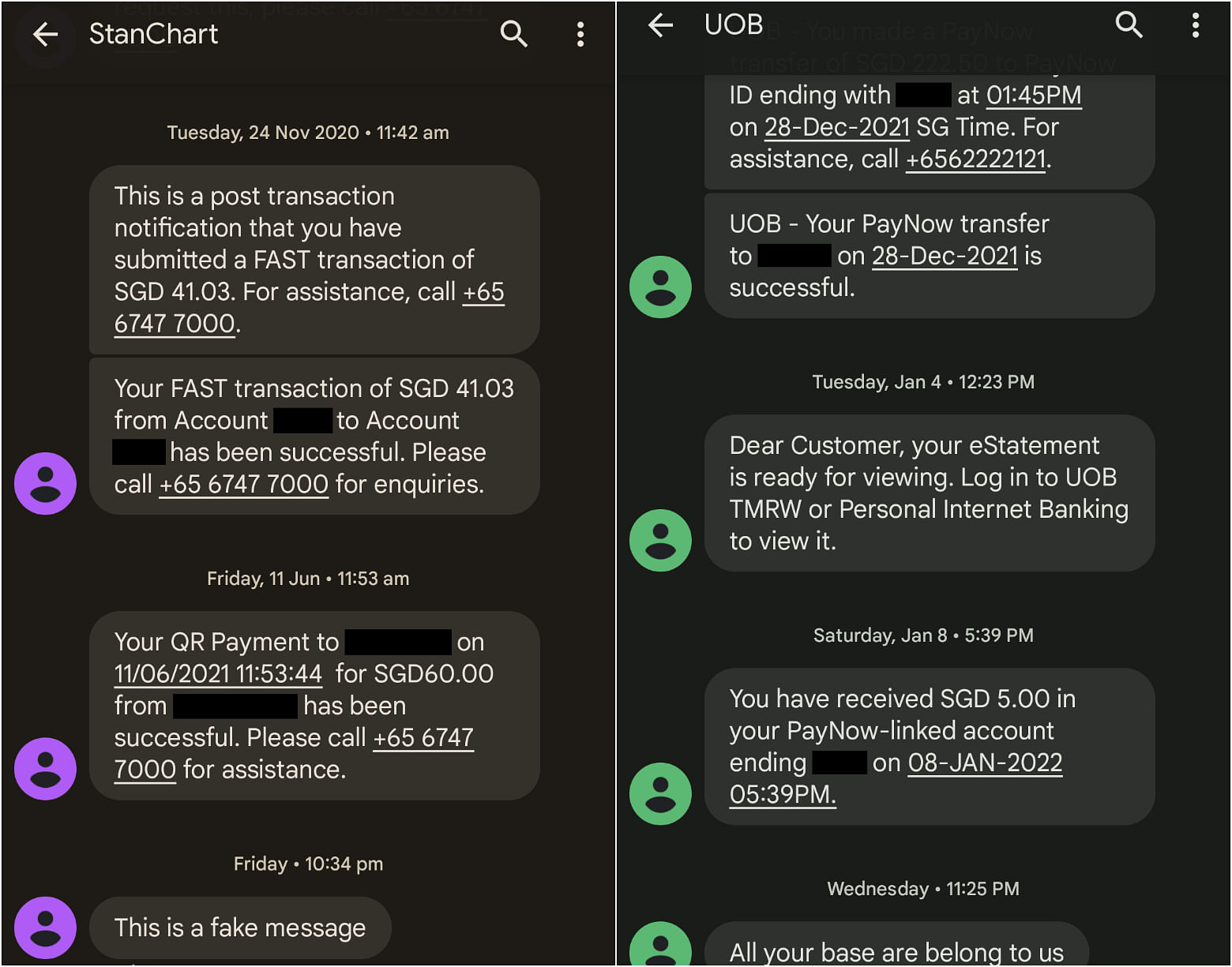
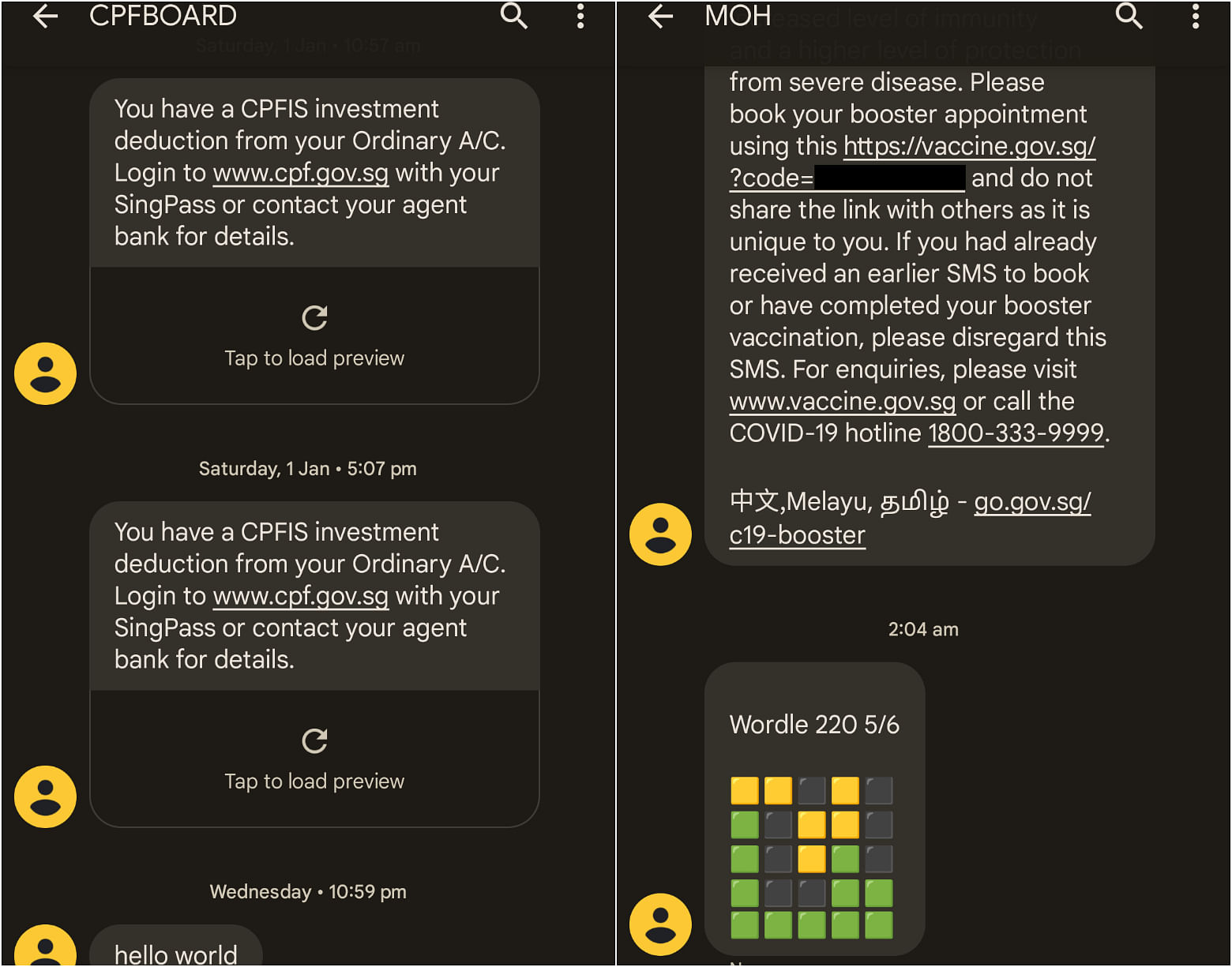
Code scrapers and Web hosts
There are also free tools that can be used to download or "scrape" a website's code, which will allow a scammer to easily recreate its appearance.
Website domains can also be bought cheaply. ST found that a one-year licence for a website ending in ".com" can be bought for $20 to $30, while one ending in ".sg" can go for about $60.
A scammer can upload the stolen website code to the Web host and quickly create a fake version of a bank's log-in page or a government website.
With some basic coding know-how, existing fields can be modified to send the information entered to the scammer's server instead of the bank's, and new fields asking for other information such as credit card details can be added.
Recognising fake messages and websites
Last week, the Monetary Authority of Singapore and the Association of Banks in Singapore announced new measures aimed at curbing SMS phishing scams.
One of them is that banks will no longer send clickable links in SMS messages. Any future links in messages purportedly sent from banks are therefore likely to be fake.
Banks, government agencies and telcos in Singapore have also indicated that they will sign up for the Infocomm Media Development Authority's SMS SenderID registry, which is designed to prevent unauthorised users from spoofing the sender IDs of banks and other institutions.
However, it is not a foolproof move. The Business Times reported last Thursday that several companies that have signed up to the registry can still have their sender IDs spoofed.
Phishing messages can also be sent by other means such as e-mail.
To avoid falling prey, do not click on links that appear to lead to websites dealing with sensitive information. Instead, use official apps to access these services or manually enter the official website address of the bank or agency into the browser.
Get The New Paper on your phone with the free TNP app. Download from the Apple App Store or Google Play Store now


